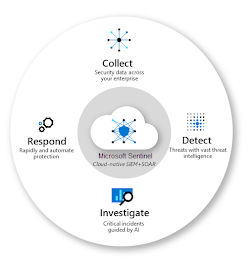
Getting Started with Microsoft Sentinel- Connect Your Data
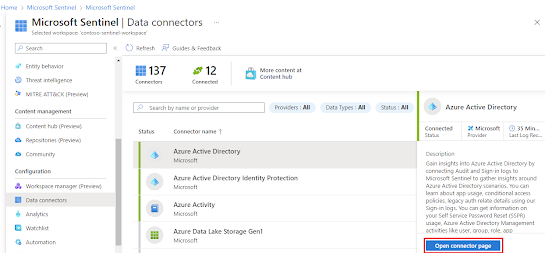
Overview Data is sent to the Microsoft Sentinel workspace after configuring the provided data connectors, which are generally present in Out-Of-The-Box (OOTB), or built-in Content Hub solutions for Microsoft 365 services, Azure, and third-party specific. Ingest Log Data with Data Connectors Connect the data sources with Microsoft Sentinel Data Connectors, which are in the Content Hub Solutions provided by Microsoft Sentinel. After installing the Content Hub Solution, the Configuration | Data Connectors menu section will show the installed Data Connectors. Now, select the Open Connector page to view the detailed connector page split in left and right halves. The left half contains all the information regarding the connector, its status, and the last time a log was received when connected. Whereas, the bottom part displays the Data Types with the lists of tables that the connector writes to. The right half has an instructions tab that can vary according to the connector, and genera...