Working With Microsoft Sentinel - Traditional SOC Challenges
Introduction
SOC (Security Operations Center) is responsible for improving an organization's threat detection and protection with the help of various cybersecurity technologies. It is a team of highly professional IT security officials, whose job is to analyze the organization's entire IT infrastructure for any security threat and take preventive measures on real-time basis.
Mainly, it can unify an organization's security tools, practices, and response to security incidents, that can surely improve preventive measures and security policies, achieve faster threat detection, cost-effective response to security threats. An SOC can also help in improving customer confidence by simply strengthening the overall IT security of an organization.
However, SOC team also faces some challenges on daily basis.
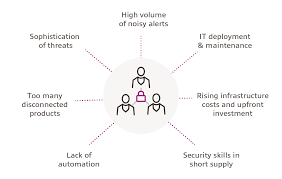
Traditional SOC Challenges
- High Volume of Security Alerts- Since, the number of security alerts are increasing by the day, a considerable amount of an analyst's time always waste upon investigating their credibility and warnings. This sometimes leads to major slip like some alerts being missed or the serious ones just sliding through the cracks. Ideally, an analyst's time should be used on finding ways to reduce he timing between breach detection and response.
- Rising Infrastructure Cost and Upfront Investment- There is always some budget constraints in every business. It is quite difficult to monitor, evaluate, and manage security operations, while simultaneously justifying the spendings. Organizations are increasing their investment in cybersecurity measures, but, how much is sufficient in this era of increased cyber threats is not easy to determine.
- Shortage of Skills and Knowledge- This is another challenge. Organizations could not find appropriately skilled officials, leaving the remaining staff to fill the void. Moreover, not knowing enough also obstructs the ability to perceive a threat at hand, since, SOC teams receives more false positive and negative responses and wastes time in tracking them.
- Sophistication of Threats- Since, the cybersecurity attackers have become more sophisticated with the skillset and tools to bypass conventional defenses (including endpoint security and firewalls), it is not easy to outsmart them in their own game.
- Too Many Disconnected Products- Generally, all the organizations have many security tools to overcome all types of cyber threats. Hence, they tend to be disconnected from each other, restricting the scope of identifying the sophisticated threats that can cut across security silos.
- Unknown Threats- The traditional signature-based detection, firewalls, and endpoint detection cannot identify an unknown threat, and it is difficult to detect and defend against zero day threats for the SOCs.
Conclusion
SOC analysts are the first line of defense in an IT infrastructure and faces many more challenges on daily basis, however, with proper resources, methodologies, and training, they can overcome these challenges and properly secure the data.



Comments
Post a Comment