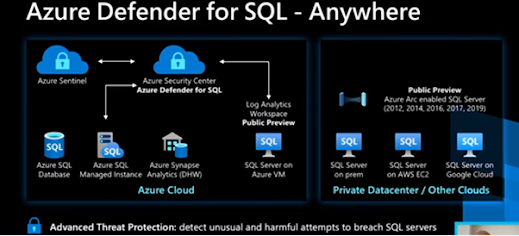
Explain Cloud Workload Protections in Azure Defender (part 4 of 4)
To read part 1 please click here To read part 2 please click here To read part 3 please click here Azure Defender for Resource Manager Azure Resource Manager is the deployment and management service for Azure which provides a management layer that allows you to create, update, and delete resources in your Azure account as well as capable of automatically monitoring the resource management operations in your organization, even if they are performed through the Azure portal, Azure REST APIs, Azure CLI, or the other Azure programmatic clients while simultaneously running advanced security analytics to detect threats and alert you about any suspicious activity. What are the benefits of Azure Defender for Resource Manager? Azure Defender for Resource Manager readily protects against issues including: Suspicious resource management operations, such as the operations from suspicious IP addresses, disabling antimalware and suspicious scripts running in VM extensio...