Getting Started with Microsoft Sentinel- Connect Your Data
Overview
Data is sent to the Microsoft Sentinel workspace after configuring the provided data connectors, which are generally present in Out-Of-The-Box (OOTB), or built-in Content Hub solutions for Microsoft 365 services, Azure, and third-party specific.
Ingest Log Data with Data Connectors
- Connect the data sources with Microsoft Sentinel Data Connectors, which are in the Content Hub Solutions provided by Microsoft Sentinel.
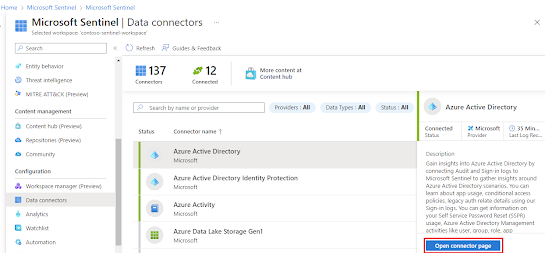
- After installing the Content Hub Solution, the Configuration | Data Connectors menu section will show the installed Data Connectors.
- Now, select the Open Connector page to view the detailed connector page split in left and right halves.
- The left half contains all the information regarding the connector, its status, and the last time a log was received when connected. Whereas, the bottom part displays the Data Types with the lists of tables that the connector writes to.
- The right half has an instructions tab that can vary according to the connector, and generally contains Prerequisites and Configuration. The Configuration tab can connect with the data source, while the Next Step tab offers a quick look through workbooks, query samples, and analytical templates. However, Data Connectors can only be disconnected or deactivated, they cannot be deleted.
Understand Data Connector Providers
Microsoft 365 Defender
It provides alerts, incidents, and raw data from Microsoft 365 Defender products including (but not limited to):
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Microsoft Defender for Cloud Apps
Microsoft Azure Services
Its connectors include (but not limited to):
- Azure AD
- Azure Activity
- Azure AD Identity Protection
- Azure DDoS Protection
- Microsoft Defender for IoT
- Azure Information Protection
- Azure Firewall
- Microsoft Defender for Cloud
- Azure Web Application Firewall (WAF)
- Domain name server
- Office 365
- Windows firewall
- Security Events
Vendor Connectors
There is an ever-growing list of vendor-specific data connectors:
- Custom connectors using the Log Analytics API- Log Analytics Data Connector API can be used to send data to the Microsoft Sentinel Log Analytics workspace.
- Logstash plugin- Microsoft Sentinel's output plugin for Logstash data collection engine can be used to send any log to the Log Analytics workspace. The logs are written to a custom table defined via the output login.
Common Event Format and Syslog Connector
The generic Common Event Format (CEF) and Syslog Connector can be used in case of no vendor-provided connector. Syslog, common to Linux, is an event logging protocol where applications send messages that may be either stored on the local machine or Syslog collector. However, Common Event Format (CEF) is an industry-standard format on top of Syslog messages, and is used by many security vendors to allow event interoperability among different platforms.
CEF has always been the first choice as log data is stored into the predefined fields of the CommonSecurityLog table, whereas, Syslog offers header fields and the raw log messages are stored in SyslogMessage field in the Syslog table. To query a Syslog data, a parser should be written to extract the specific field.
View Connected Hosts
The Data Connector page shows the installed connectors and to view the connected hosts, following steps should be taken:
- Select Settings
- Workspace settings transfers to Log Analytics
- Now, select Agents in the Log Analytics Settings area
- Two tabs will be displayed, one for Windows and another one for Linux.



Comments
Post a Comment