Working with Microsoft Sentinel- Cloud-Native SIEM and SOAR For Intelligent Security Analytics For Your Entire Enterprise
What is Microsoft Sentinel?
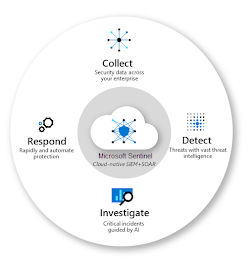
Microsoft Sentinel is a scalable cloud-native solution. It provides intelligent security analytics and threat intelligence across the enterprise. It is a one stop solution for threat detection, threat visibility, threat proactive hunting, and threat response. It can perform following tasks:
- It can collect data at cloud scale across all users, devices, applications, etc., both on-premises and multiple clouds.
- It can also detect a previously undetected threat via Microsoft's analytics and threat intelligence, simultaneously minimizing false positives.
- It is capable of investigating threats with artificial intelligence and hunt for any other suspicious activities.
- It has a rapid response to threat incidents due to the built-in orchestration and automation of common tasks.
Collects Data Via Data Connectors
In order to onboard Microsoft Sentinel, it is required to connect with the data sources. It consists of various connectors for Microsoft solutions to offer real-time integration. Some of them are:
- Microsoft sources like Microsoft 365 Defender, Microsoft Defender for Cloud, Office 365, Microsoft Defender for IoT, etc.
- Azure service sources such as Azure AD, Azure Activity, Azure Storage, Azure Key Vault, etc.
The built-in connectors broadens the security and applications ecosystems for non-Microsoft solutions. Common event format, Syslog, or REST-API can also be used for connecting the data sources with Microsoft Sentinel.
Create Interactive Reports by Using Workbooks
When the onboarding is done, the data can be monitored via the integration with Azure Monitor workbooks. Microsoft Sentinel also contains built-in workbook templates for reference and permits to create custom workbooks across the data. These workbooks are generally used by SOC engineers and analysts of all tiers to visualize data. They are the best for high-level Microsoft Sentinel data and does not require coding knowledge. However, they cannot be integrated with an external data.
Correlate Alerts Into Incidents by using Analytical Rules
Microsoft Sentinel makes use of analytics to correlate alerts to incidents, in order to minimize the noise and number of alerts. Incidents are groups of related alerts that can point towards a possible threat and immediately needs to investigated and resolved. The built-in correlation can be used either as they are or as a starting point to build a new one. Machine learning rules are provided to map the network's behavior and find anomalies (if any), by combining low fidelity alerts of different entities into potential high-fidelity security incidents.
Automate and Orchestrate Common Tasks by Using Playbooks
The automation and orchestration solution offers a highly extensible architecture capable of scalable automation for novel technology threats. Playbooks can created via Azure Logic Apps from a constantly expanding gallery with hundreds of connectors for various services and systems. These connectors will help in applying any custom logic in a workflow, such as, ServiceNow, Jira, Zendesk, Slack, etc. Playbooks are used by SOC engineers and analysts of all tiers to automate and simplify tasks including data ingestion, enrichment, investigation, and remediation. They are the best with single, repeatable task, and does not require coding knowledge. However, they should not be used for complex task chains or ad-hoc, or for documenting and sharing evidence.
Investigate the Scope and Root cause of Security Threats
The deep investigation tools of Microsoft Sentinel, helps in understanding the scope and root cause of a potential security threat. On an interactive graph, an entity can be chosen to ask questions to know more and get to the root cause of the threat.
Hunt for Security Threats via Built-in Queries
The powerful hunting search-and-query tools of Microsoft Sentinel are based on MITRE framework. They help in proactive search for security threats across an organization's data sources before triggering of an alert. Custom-made detection rules can be created according to the hunting queries and can then be used as alerts for the security incident responders.
Enhance Threat Hunting with Notebooks
Jupyter notebooks are supported by Microsoft Sentinel in Azure Machine learning workspaces. They increases the scope of using the Microsoft Sentinel data. For example, certain tasks can be done like performing analytics or creation of data visualizations, that are not built-in to Microsoft Sentinel. Notebooks are used by threat hunters or Tier 2-3 analysts , incident investigators, data scientists, and security researchers. However, a higher learning curve and coding knowledge are required, and the automation support is also limited. Notebooks are the best for more complex chains of tasks, ad-hoc procedural controls, machine learning and custom analysis.
Download Security Content from Community
Microsoft Sentinel community is a powerful resource and the security analysts create as well as post new workbooks, playbooks, hunting queries, etc., on it. A sample content can be easily downloaded from the private community GitHub repository to create custom workbooks, hunting queries, etc., for Microsoft Sentinel.



Comments
Post a Comment