Role Based Access Control (RBAC) (part 1 of 3)
Plan for RBAC
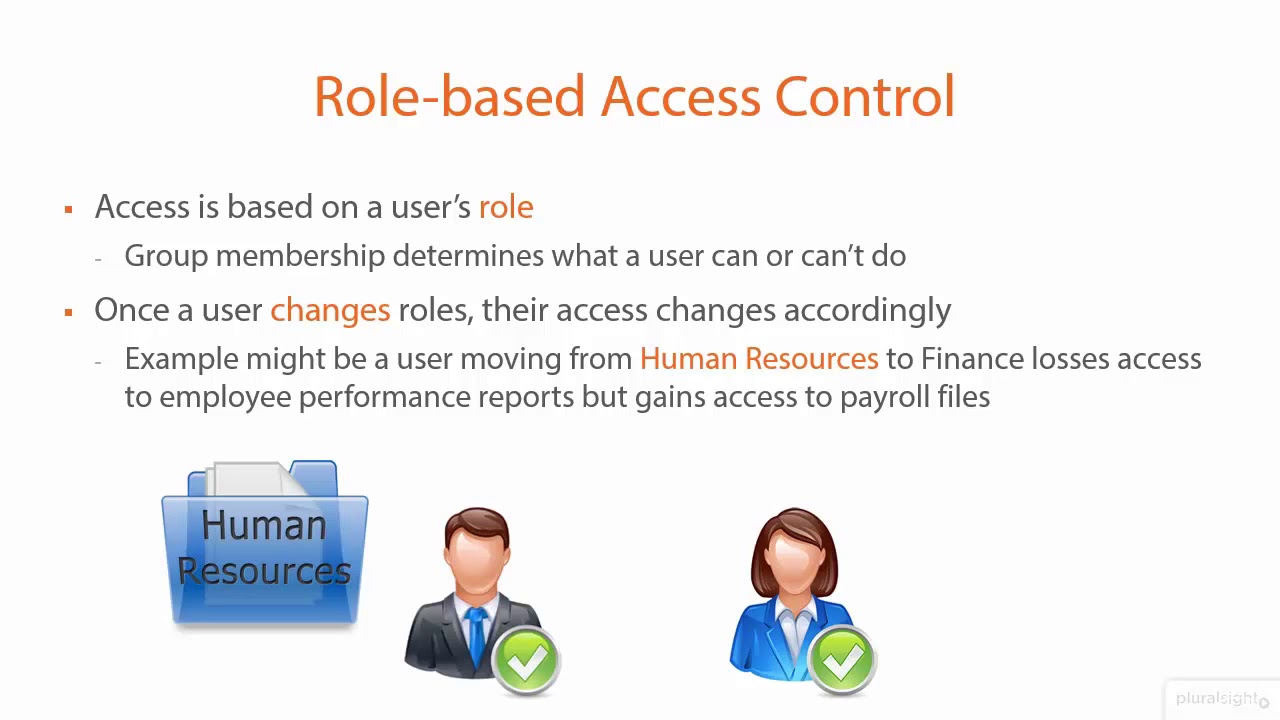
What can I do with RBAC?
- Allow one user to manage virtual machines in a subscription and another to manage virtual networks.
- Allow a DBA group to manage SQL databases in a subscription.
- Allow a user to manage all the resources in a resource group, like VMs, websites, and subnets.
- Allow an application to access all resources in a resource group.
How RBAC works?
Security Principal
- User- It's an individual having a profile in Azure AD and various roles can also be assigned to the users in the other tenants.
- Group- It's a set of users created in Azure AD and if a role is assigned to a group, then, all the users within that group will have that role.
- Service principal- It's a security identity used by applications or services to access specific Azure resources and it may also be considered as a user identity (username and password or certificate) for an application.
Role Definition
It's a collection of permissions and sometimes called just role. Role definition consists of the operations that can be performed like read, write, and delete. Roles can be either high-level like owner or specific like VM reader. Azure contains following built-in roles and the first three applies to all resource types:
- Owner Has full access to all resources including the right to delegate access to others.
- Contributor Can create and manage all types of Azure resources but can't grant access to others.
- Reader Can view existing Azure resources.
- User Access Administrator Allow you to manage user access to Azure resources.
The other built-in roles helps you to manage specific Azure resources and if they doesn't meet the specific need of your organization, you can create your own custom roles.
Scope
It's the boundary applied to the access i.e. you can limit the actions allowed by defining a scope while assigning a role which can be helpful to make someone a Website Contributor, but only for one resource group. Scope can be specified at multiple levels- management groups, subscription, resource group, or resource and are structured in a parent-child relationship. When you grant access at a parent scope, those permissions are inherited to the child scopes, for example:
- If you assign the Owner role to a user at the management group scope, that user can manage everything in all subscriptions in the management group.
- If you assign the Reader role to a group at the subscription scope, the members of that group can view every resource group and resource in the subscription.
- If you assign the Contributor role to an application at the resource group scope, it can manage resources of all types in that resource group, but not other resource groups in the subscription.
How RBAC determines if a user has access to a resource?
- A user (or service principal) acquires a token for Azure Resource Manager which includes user's group memberships (including transitive group memberships).
- The users makes a REST API call to Azure Resource Manager with the token attached.
- Azure Resource Manager retrieves all the role assignments and deny assignments that apply to the resource upon which the action is being taken.
- Azure Resource Manager narrows the role assignments that apply to this user or their group and determines what roles the user has for this resource.
- Azure Resource Manager determines if the action in the API call is included in the roles the user has for this resource.
- If the user doesn't have a role with the action at the requested scope, access is not granted. Otherwise, Azure Resource Manager checks if a deny assignment applies.
- If a deny assignment applies, access is blocked. Otherwise access is granted.



Comments
Post a Comment