Identity Governance (part 1 of 6)
Azure AD Identity Governance
- Govern the identity lifecycle
- Govern access lifecycle
- Secure privileged access for administration
It can also help the organizations to address the following key questions:
- Which users should have access to which resources?
- What are those users doing with that access?
- Are there effective organizational controls for managing access?
- Can auditors verify that the controls are working?
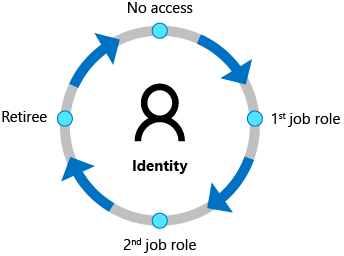
Identity Lifecycle
Identity lifecycle management is known as the foundation for Identity Governance and its effective use requires a proper modernization of the identity lifecycle management infrastructure for applications. Azure AD premium can automatically maintain the user identities for people represented in Workday in both AD as well as Azure AD and also includes Microsoft Identity Manager to import records from the on-premises HCM (Human Capital Management) systems like SAP, Oracle eBusiness, Oracle PeopleSoft.
While Azure AD B2B Collaboration allows you to share your organization's applications as well as services with the guest users and external partners from any organization securely along with the maintenance of control over your own corporate data; the Azure AD entitlement management helps you to choose the type of organization users are allowed to request access and can be added as B2B guests to your organization's directory and making sure that these guests will be removed when no longer required.
Access Lifecycle
Technologies can readily help the organizations in the automation of the access lifecycle process along with the ability to control which guest users can have access to an on-premises applications whose rights can be regularly reviewed with the help of recurring Azure AD access reviews. If a user tries to access applications, Azure AD can enforce Conditional Access policies which may include displaying a terms of use and making sure that the user has agreed to the terms before accessing an application.
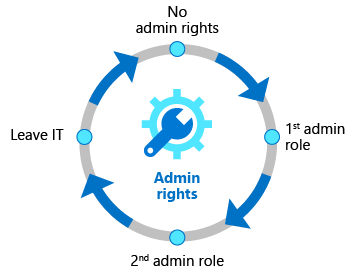
Privileged Access Lifecycle
Although privileged access has been stated as a separate capability from Identity Governance by various vendors but Microsoft thinks it as the key of Identity Governance. Azure AD Privileged Identity Management (PIM) offers additional controls made to secure access rights for resources across Azure AD, Azure, and the other Microsoft Online Services. It provides just-in-time access as well as role change alert capabilities along with the multi-factor authentication and Conditional Access; to offer a comprehensive set of governance controls to secure your company's resources. However, the organizations can use access reviews to configure recurring access recertification for all the users in administrator roles in other forms of access.





Comments
Post a Comment