Identity Governance (part 2 of 6)
Conditional Access Explained
Common Scenarios
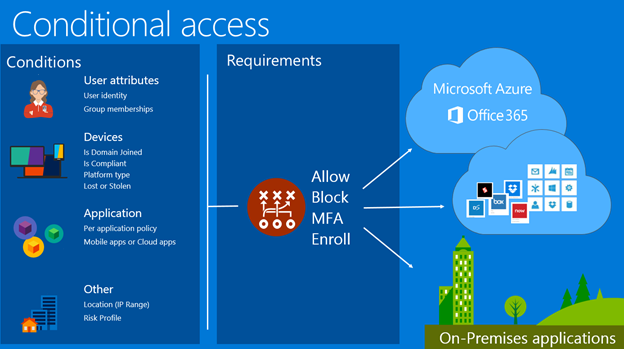
Conditional access policies allows you to apply right access controls under the required conditions while also providing you with extra security when needed and vice versa. It can easily help you with the following:
- Sign-in risk- Azure AD Identity Protection detects sign-in risks. How do you restrict access if a detected sign-in risk indicates a bad actor? What if you would like to get stronger evidence that sign-in was performed by the legitimate user? What if your doubts are strong enough to even block specific users from accessing an app?
- Network location- Azure AD can be accessed from anywhere. What if an access attempt is performed from a location that's not controlled by your IT department? A combination of username and password may be enough as a proof of identity for access attempts from your corporate network, but what if you want a stronger proof of identity for access attempts that are initiated from other unexpected countries or regions of the world or if you want to block them from certain locations?
- Device management- In Azure AD, users can easily access cloud apps from a broad range of devices including mobile as well as personal devices. What if you want the access attempts should only be performed by the devices that are managed by your IT department or you want to block certain types of devices from accessing your cloud apps in your environment?
- Client application- Nowadays, you can easily access multiple cloud apps with the help of different app types like web-based apps, mobile apps, or desktop apps. What if an access attempt is performed using a client app type that causes known issues? What if you require a device that is managed by your IT department for certain app types?
Conditional Access Policies
|
When this happens |
Then do this |
Then do this represents the response of your policy. Conditional Access policy allows you to control how authorized users can access cloud apps under specific conditions while you can respond by enforcing additional requirements like multi-factor authentication, a managed device, and others; these requirements are known as access controls.
When this happens determines the reason for triggering your policy which can be characterized by a group of conditions that have been satisfied. However, the following two mandatory assignment conditions play a special role in Azure AD Conditional Access:
- Users- The users performing an access attempt (Who).
- Cloud apps- The targets of an access attempt (What).
You can also include additional conditions that can describe how the access attempt is performed. The main objective of a conditional access policy is to enforce additional access controls on an access attempt to a cloud app based on how an access attempt is performed.
A policy-based approach to protect access to your cloud apps enables you to start drafting the policy requirements for your environment with the help of the given structure without worrying about the technical implementation.



Comments
Post a Comment