Mitigate Incidents Using Microsoft 365 Defender (part 2)
To read part 1 please click here
Use the Microsoft Security Center Portal
- Home- Get an at-a-glance view of the overall security health of your organization.
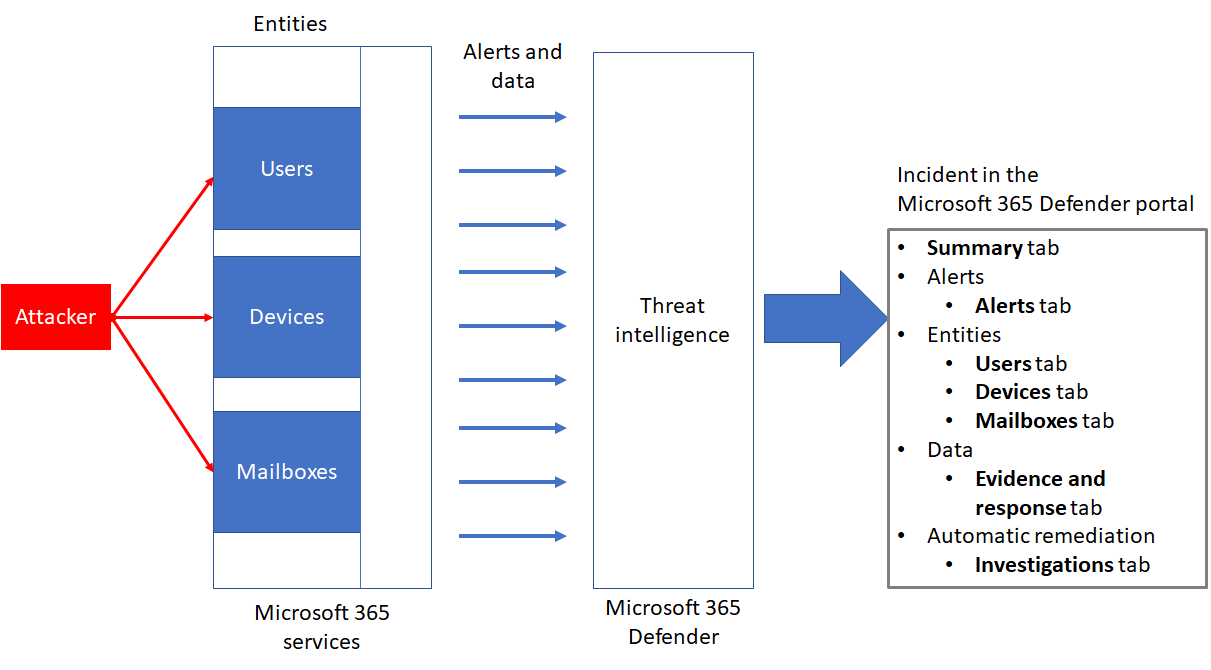
- Incidents- See the broader story of an attack by connecting the dots seen on an individual alerts on the entities. You'll know exactly where an attack started, what devices are impacted, who was affected, and where the threat has gone.
- Action center- Reduce the volume of the alerts your security team must address manually, allowing your security operations team to focus on the more sophisticated threats and the other high-value initiatives.
- Reports- Get the detail and information you need to better protect your users, devices, apps, and more.
- Secure score- This page provides an all-up summary of the different security features as well as capabilities you have enabled and includes recommendations for the areas to improve.
- Hunting- Proactively search for the malware, suspicious files, and activities in your Microsoft 365 organization.
- Classification- Helps protect the data loss by adding labels to classify the documents, email messages, sites, and more. When a label is applied, the content or site is protected based on the settings you choose.
- Policies- Set up policies to manage the devices, protect against threats, and receive alerts about various activities in your organization.
- Permissions- Manages who in your organization has access to view the content and perform tasks in the Microsoft 365 Security Center. You can also assign the Microsoft 365 permissions in the Azure AD Portal.
The Microsoft Security Center Portal is the central location to manage the integrated Microsoft security solutions.
Manage Incidents
Incidents from the last 30 days are shown in the incident queue and from there the security defenders can see which incident should be prioritized based on the risk level and other factors. Security Defenders can also rename the incidents, assign them to the individual analyst, classify, and add tags to incidents for a better as well as more customized incident management experience.
Prioritize Incidents
The incidents queue shows a collection of flagged incidents from across the devices, users, and mailboxes. By default, the queue in the Microsoft 365 Security Center displays incidents seen in the last 30 days which helps you to make an informed decision regarding the prioritization of the incidents to handle.
For more clarity at a glance, automatic incident naming generates the incidents names based on the alerts attributes such as the number of the endpoints affected, users affected, detection sources, or categories which allows you to quickly understand the scope of the incident.
Use the Action Center
- Approving pending remediation actions
- Viewing an audit log of already approved remediation actions
- Reviewing completed remediation actions
In the Action Center, you'll see two tabs:
- The Pending tab, which lists investigations that require review and approval by someone in your security operations team to continue. Make sure to review and take action on the pending items you see here.
- The History tab, which lists past investigations and remediation actions that were taken automatically. You can easily view data for the past day, week, month, or six months.
Available Actions
As remediation actions are taken, they're listed on the history tab in the Action Center. Such actions includes the following:
- Collect investigation package
- Isolate device (this action can be undone)
- Offboard machine
- Release code execution
- Release from quarantine
- Request sample
- Restrict code execution (this action can be undone)
- Run antivirus scan
- Stop and quarantine
Action source
|
Action source value |
Description |
|
Manual
device action |
A
manual action taken on a device. Examples includes device isolation or file
quarantine. |
|
Manual
email action |
A
manual action taken on an email. An example includes soft-deleting email
messages or remediating an email message. |
|
Automated
device action |
An
automated action taken on an entity, such as a file or process. Examples of
an automated action includes sending a file to quarantine, stopping a
process, and removing a registry key. |
|
Automated
email action |
An
automated action taken on an email content, such as an email message, attachment,
or URL. Examples of an automated actions includes soft-deleting email
messages, blocking URLs, and turning off an external mail forwarding. |
|
Advanced
hunting action |
Actions
taken on the devices or an email with advanced hunting. |
|
Explorer
action |
Action
taken on an email content with the explorer. |
|
Manual
live response action |
Action
taken on a device with live response. Examples including deleting a file,
stopping process, and removing a scheduled task. |
|
Live
response action |
Action
taken on a device with the Microsoft Defender for Endpoint APIs. Examples of the
actions includes isolating a device, running an antivirus scan, and getting
information about a file. |
To read part 1 please click here



Comments
Post a Comment