Database Security (part 3 of 4)
Vulnerability Assessment
SQL Vulnerability Assessment is an easy-to-configure service that can discover, track, as well as help you remediate potential database vulnerabilities and provides visibility into your security state. It can help you:
- Meet compliance requirements that require database scan reports.
- Meet data privacy standards.
- Monitor a dynamic database environment where changes are difficult to track.
View the report
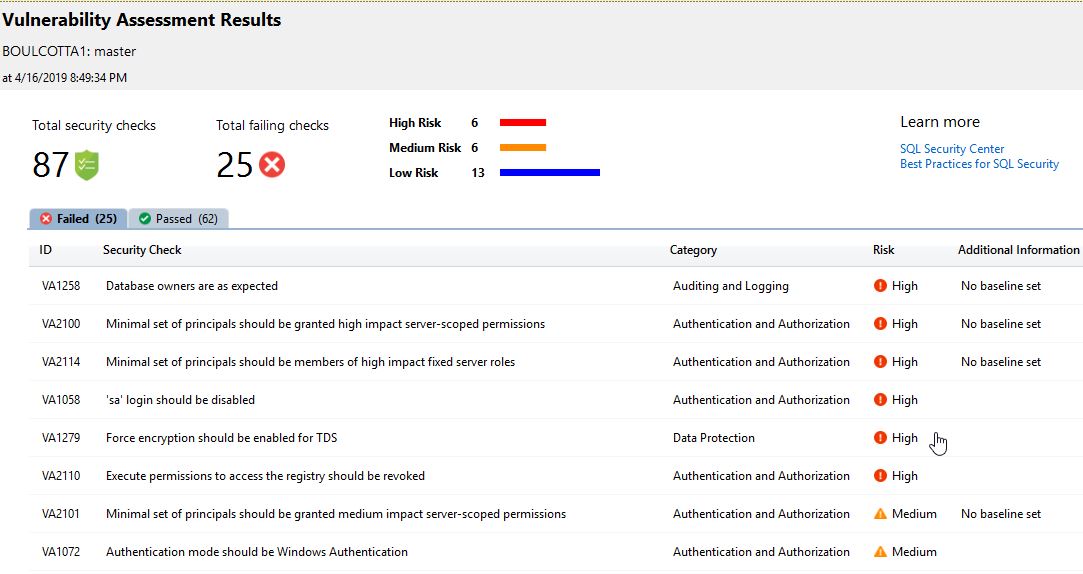
When your scan is finished, your scan report is automatically displayed in the Azure portal which presents an overview of your security state. The results includes warnings on deviations from the best practices and a snapshot of your security-related settings, such as database principles and roles as well as their associated permissions while the report also provides a map of sensitive data discovered in your database including recommendations to classify that data by using data discovery and classification.
Scan results are shown below:
Set your baseline
Advanced Threat Protection
ATP provides a new layer of security, which enables customers to detect and respond to potential threats as they occur by providing security alerts on anomalous activities.
Advanced threat protection alerts
- Vulnerability to SQL injection- This alert is triggered when an application generates a faulty SQL statement in the database. There are two possible reasons for the generation of a faulty statement, either it is a defect in application code that constructs the faulty SQL statement, or, the application codes or stored procedures don't sanitize user inputs when constructing the faulty SQL statement, which may be exploited for SQL injection.
- Potential SQL injection- This alert is triggered when an active exploit happens against an identified application vulnerability to SQL injection. This means the attacker is trying to inject malicious SQL statements using the vulnerable application code or stored procedures.
- Access from unusual location- This alert is triggered when there is a change in the access pattern to SQL server, where someone has logged on to the SQL server from an unusual geographical location.
- Access from unusual Azure data center- This alert is triggered when there is a change in the access pattern to SQL server, where someone has logged on to the SQL server from an unusual Azure data center that was seen on this server during the recent period.
- Access from unfamiliar principle- This alert is triggered when there is a change in the access pattern to SQL server, where someone has logged on to the SQL server using an unusual principle (SQL user).
- Access from a potentially harmful application- This alert is triggered when a potentially harmful application is used to access the database.
- Brute force SQL credentials- This alert is triggered when there is an abnormal high number of failed logins with different credentials.
ATP is integrated with Azure Security Center to detect and respond to the potential threats as they occur.
.png)



Comments
Post a Comment