Identity Providers & Federation (Part 1)
To read part 2, please click here
About Web Identity Federation
Web Identity Federation allows the users of your app to sign-in with the help of a well-known identity provider (IdP) like Amazon, Google, Facebook, etc. In this process, an authentication token is given, which can be exchanged for temporary security credentials in AWS that can map to an IAM role with permissions to use the resources in your account. Hence, IdP will help you keep your AWS account safe as you don't have to embed and distribute long-term security credentials with your application.
It's recommended to use Amazon Cognito, because it acts as an identity broker and does much of the federation work for you. Otherwise, you have to write a code that can easily interact with a web IdP, and then calls the AssumeRoleWithWebIdentity API to trade with the received identity token.
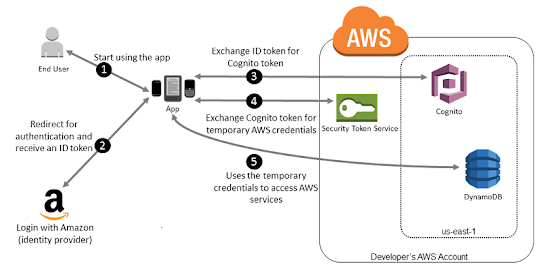
Using Amazon Cognito for Mobile Apps
- Firstly, a customer starts your app on a mobile device, and it asks to sign-in.
- The app uses Login with Amazon resources to accept the user's credentials.
- Now, the app will use Amazon Cognito API operations GetID and GetCredentialsForIdentity to exchange the Login with Amazon ID token for an Amazon Cognito Token.
- After that, the app will get temporary security credentials from Amazon Cognito.
- The temporary security credentials can be used by the app to access any AWS resources required by the app to operate.
Now, in order to configure your app using Amazon Cognito, use the following process:
- Firstly, you have to sign-up as a developer with login with Amazon, Google, Facebook, or any other OpenID Connect (OIDC) and configure one or more apps with the provider. However, this step is optional as Amazon Cognito also supports unauthenticated access for your users.
- Now use the Amazon Cognito wizard (in the AWS Management Console) to create an identity pool that can keep your end user identities organized for your apps.
- Integrate AWS Amplify with your app, and import the files required to use Amazon Cognito.
- After that, you have to create an instance of the Amazon Cognito credentials provider, passing the identity pool ID, your AWS account number, and the Amazon Resource Name (ARN) of the roles that you associate with the identity pool.
- After your apps' successful access of an AWS resource, you can pass the credential provider instance to the client object, that can pass temporary security credentials to the client whose permissions are based on the roles or role defined earlier.
To read part 2, please click here




Comments
Post a Comment