Manage Device Access (part 2)
To read part 1, please click here
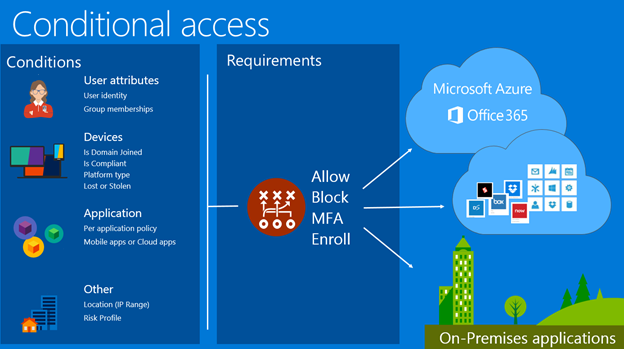
Create a Conditional Access Policy
- Assignments
- Users & groups- It specifies users, groups, and directory roles for which the policy applies, or which are excluded from the policy.
- Cloud apps- It specifies the cloud apps for which access is controlled by the conditional access policy.
- Conditions- They define when the policy will apply including sign-in risks, device platforms, locations, client apps, and device state.
- Access controls
- Grant- This control either blocks access or specifies additional requirements which need to be satisfied to allow access including requirements like MFA or compliant device.
- Session- It can enable limited experiences within a cloud app like app enforced restrictions.
Conditional Access with Intune
Note: Conditional access is an Azure AD capability included with an Azure AD Premium license and Intune can enhance this capability by adding mobile device compliance and mobile app management to the solution.
Device-based conditional access
Intune and Azure AD combined ensures that only managed and compliant devices are allowed access to email, Office 365 services, Software as a Service (SaaS) apps, and on-premises apps. You can also set a policy in Azure AD to only enable computers that are domain-joined, or mobile devices that are enrolled in Intune to access Office 365 services.
Intune offers device compliance policy capabilities that can evaluate the compliance status of the devices which is reported to Azure AD that uses it to enforce the conditional access policy created in Azure AD when the user tries to access company resources. Device-based conditional access policies for Exchange online and the other Office 365 products are configured through the Azure portal.
App-based conditional access
Intune app protection policies protects your company data on the devices that are enrolled into Intune. These policies can also be used on an employee owned devices that are not enrolled for management in Intune, however, you still need to ensure that company data and resources are protected.
App-based conditional access and client app management adds a security layer by ensuring that only client apps that support Intune app protection policies can access Exchange online and other Office 365 services. However, if you want to create an app-based conditional access policy, you must have:
- Enterprise Mobility + Security (EMS) or an Azure AD Premium subscription
- Users must be licensed for EMS or Azure AD
Monitor Enrolled Devices
You can also trigger a device action and view history of the remote action that were run on different devices along with the action, its status, who initiated the action, and the time on the Intune blade. The remotely triggered actions on a device highly depends on the device type and includes the following:
- Remove company data
- Factory reset
- Remote lock
- Reset passcode
- Bypass Activation Lock (only for iOS devices)
- Fresh Start (only for Windows)
- Lost mode (only for iOS devices)
- Locate device (only for iOS devices)
- Restart (only for Windows devices)
- Windows 10 PIN reset
- Remote control for Android
- Synchronize device
MDM for Office 365 can also be used to monitor enrolled devices and to perform device management tasks as it supports a subset of functionality provided by Intune. The following device management tasks can be performed in MDM for Office 365:
- Wipe a device
- Block unsupported devices from accessing Exchange email using Exchange ActiveSync
- Set up device policies like password requirements and security settings
- View list of blocked devices
- Unblock noncompliant or unsupported device for a user or group or users
- Get details about the devices
- Remove users so their devices are no longer managed by MDM
To read part 1, please click here



Comments
Post a Comment