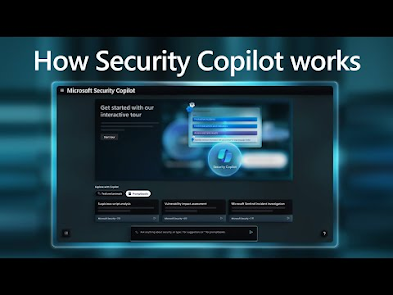
Zero Trust Principles in Microsoft Security Copilot

Introduction Every connection and resource request is handled by Zero Trust security approach as if it came from a malicious actor and an uncontrolled network. No matter the source of the request or resource it uses, Zero Trust encourages us to "never trust, always verify." In order to apply Zero Trust principles for Microsoft Security Copilot five layers of protection should be applied. The five steps are discussed below: Step 1: Deploy or validate identity and access policies for admin and SecOps staff The first step is to stop bad actors from gaining access to Security Copilot so they can't use it to quickly learn about cyberattacks. Users must change their passwords when high-risk activity is identified, and their accounts must use multifactor authentication (MFA) to prevent access from being compromised by simple password guessing. Intune management and device compliance policies must be followed by devices. These recommendations align with the Specia...